Security Features
Industry leading technology
Regardless of how unimportant you think your data is, someone out there may attempt to steal it and use it against you. Our system values your security above all else and we are committed to ensuring your privacy at all times using the strongest encryption algorithms available.


No Backdoor
There is no “secret entrance” or method that would allow anyone to access your secure data with our system. When we say there is no way for anyone else to access your data but you, we mean it.

Secure Endpoints
We stay on top of any potential threats by maintaining secure endpoints. With Ghost, you never have to worry about potentially dangerous individuals penetrating our system, we prevent them from ever coming close to any user data.

Perfect Forward Secrecy
Unique ephemeral encryption keys provide security for all calls and messages sent and received by your device.

End-to-End Encryption
From your device to your recipient’s, messages are completely secure. There is no way for anyone to view your private communication, no matter how hard they may try.
Double Ratchet Algorithm
Key Exchange utilizes the Double Ratchet Algorithm which combines the cryptographic ratchet based on the Diffie-Hellman key exchange and a ratchet based on the key derivation function.

User Controlled Keys
All communications are secured by your unique encryption key owned by the user. Private keys are generated and only stored on the user’s device.
Maximum Password Attempt Limit
Limit the number of incorrect password attempts to keep your data protected in case you lose your device or someone attempts to gain access to your information.

Independently Audited
With constant independent expert oversight, we are certain that our system is as secure as it can possibly be. We frequently have our protocols peer reviewed by leading industry experts and constantly upgrade our systems to improve the security of our users.
Cybercrime Happens Every Day
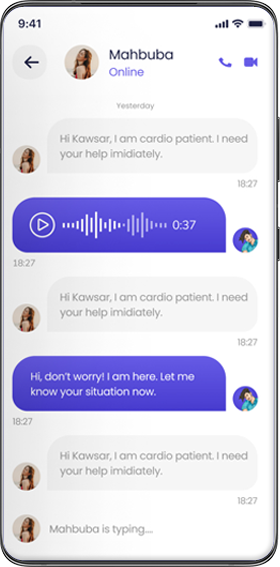
Many people undervalue their personal information. However, thieves see the value in this information and thus, cybercrime has become an extremely common problem in the world today. As your reading this right now, someone is having their identity stolen by a cybercriminal.

Encryption means that your information will remain private. Any encrypted messages you send will only be seen by your intended recipient and no one else.
Borrowing from the leaders in cryptography and security around the world, Ghost has created a unique secure system that encompasses both PGP and Elliptical Curve Cryptography that is second to none.
Post Quantum Encryption
Communication data is secured against cyberattacks using Curve25519, Double Ratcheting and Extended Triple Diffie-Hellman. Advanced PGP encryption than Encrochat.
Argon2
With Argon 2, hackers have no way of guessing passwords by using multiple, parallel rounds of memory and computer hashing which prevents any cyberattacks.
Contact Verification
Protect against Man-In-The-Middle attacks by verifying the identity of new contacts and authenticating their keys used for end-to-end encryption.
Protect your data today
Protect your personal data and security today with the strongest encryption and security safeguards implemented by our infrastructure
